Existing Clients: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support
in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.
OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
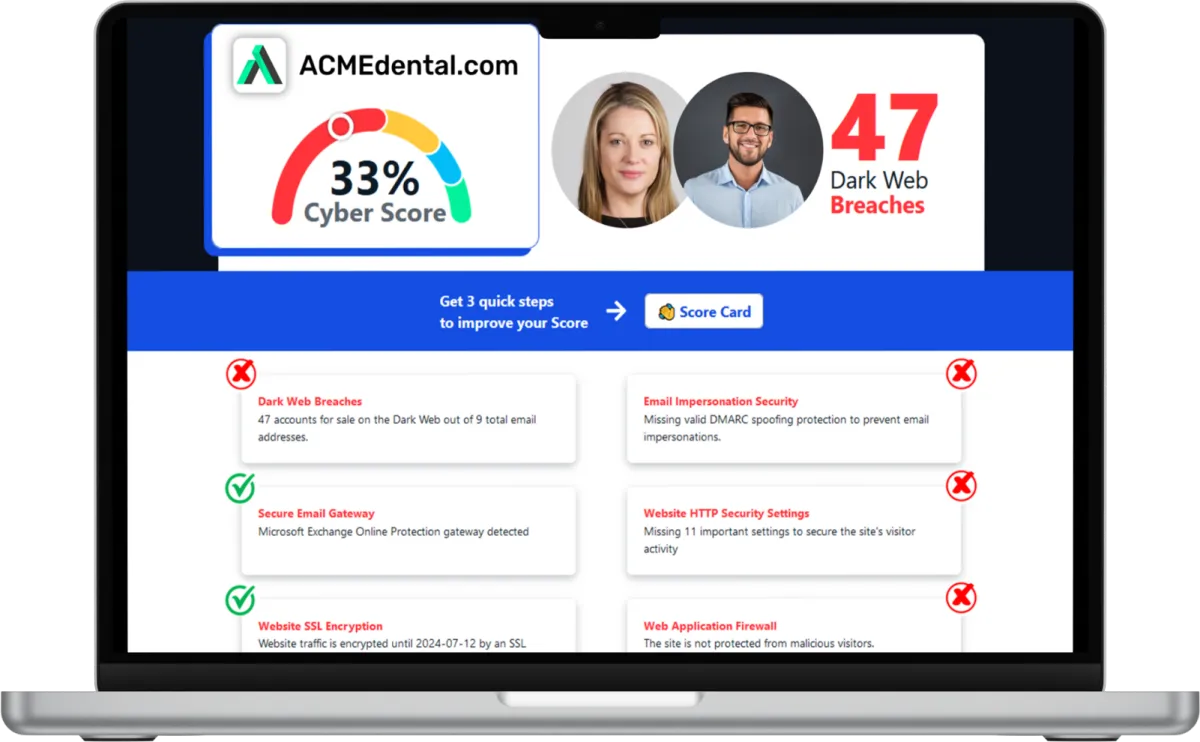
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

Cybersecurity for Remote Teams: Tips to Keep Your Business Safe
The rise of remote and hybrid work arrangements has been a game-changer for businesses of all sizes. From increased productivity and flexibility to cost savings, the benefits of remote work are undeniable. However, this shift has also brought about new challenges for businesses - one of the biggest being cybersecurity.
In a traditional office setting, businesses have greater control over their network and devices. However, with the decentralization of work, employees are now connecting to company networks from different locations and using personal devices. This opens up a whole new world of vulnerabilities for cybercriminals to exploit.
So, how can businesses keep their data and systems safe while employees work remotely? In this post, we'll explore the risks remote work poses and the steps companies can take to mitigate them.
What Are the Cybersecurity Risks of Remote Work?
Remote work introduces a range of cybersecurity risks that businesses must proactively address. Here are some of the most pressing threats:
Phishing Scams
With employees working from different locations, it becomes harder for businesses to control the flow of sensitive information. Cybercriminals take advantage of this by sending phishing scams disguised as legitimate emails, hoping to trick employees into sharing confidential data. These attacks can lead to data breaches, financial losses, and reputational damage.
Unsecured Wi-Fi Networks
When employees work remotely, they often connect to unsecured public Wi-Fi networks. A recent survey by Wrike found that 58% of employees admit they have considered connecting to public Wi-Fi for work-related tasks. Unfortunately, these networks are a breeding ground for cyberattacks, leaving company data vulnerable to interception and theft.
Weak Passwords & Poor Authentication Practices
Working remotely can lead to employees becoming lax with password and authentication practices. They may use easy-to-guess passwords, reuse the same password for multiple accounts, or leave their devices unlocked. This can result in unauthorized access to company systems and sensitive data.
Shadow IT
Shadow IT refers to the use of unauthorized software or hardware within a company. With remote work, employees have more autonomy over the technology they use, which can lead to the adoption of unapproved tools and applications. This creates security blind spots for businesses, as they may not have proper controls or visibility over these tools.
How to Strengthen Cybersecurity for Remote Teams
To mitigate the risks associated with remote work, companies should implement strong cybersecurity measures. Here are a few key steps to consider:
Create a Robust Remote Work Security Policy
A clear and comprehensive remote work security policy is essential for keeping company data safe. This policy should outline:
The use of company-approved devices and software
Password and authentication requirements
Guidelines for accessing company data and systems
Protocols for reporting security incidents or concerns
By outlining expectations and guidelines, employees can better understand their roles in maintaining cybersecurity.
Provide Secure Remote Access Solutions
One of the most effective ways to protect data is through a virtual private network (VPN). A VPN creates an encrypted connection between an employee's device and the company network, shielding data from potential threats on public Wi-Fi networks. Companies can also consider implementing multi-factor authentication for added security.
Educate Employees on Cybersecurity Best Practices
The human element is often a weak link in cybersecurity, as employees can unknowingly open the door to cyberattacks through careless actions. Companies should conduct regular training sessions to educate employees on best practices for staying safe online. This may include how to:
Identify phishing emails
Create strong passwords
Securely share sensitive information
Utilize Secure Communication & Collaboration Tools
In remote work environments, employees often rely on communication and collaboration tools such as email, messaging apps, or video conferencing. These tools should be carefully vetted to ensure data is protected.
Create an Incident Response Plan
In the event of a cybersecurity incident, it is crucial to have an established plan in place. This should include steps for:
Identifying and containing the threat
Notifying the appropriate parties
Restoring systems and data
Why Professional Support May Be the Right Choice
Managing cybersecurity for a remote team can be daunting, especially for small businesses with limited resources and expertise. In such cases, seeking professional support from a cybersecurity provider may be the best option. These experts have the knowledge and tools necessary to assess and manage potential risks, as well as provide ongoing support for a company's cybersecurity needs.
Secure Your Remote Work Environment Today
The shift to remote work doesn't have to compromise your business's security. By understanding the risks and implementing these best practices, you can create a safer environment for your team, no matter where they work.
Remote work is here to stay—don't let cybersecurity be the weak link in your strategy. Take action today to secure your business for tomorrow.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!


































