Client Support: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.

OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
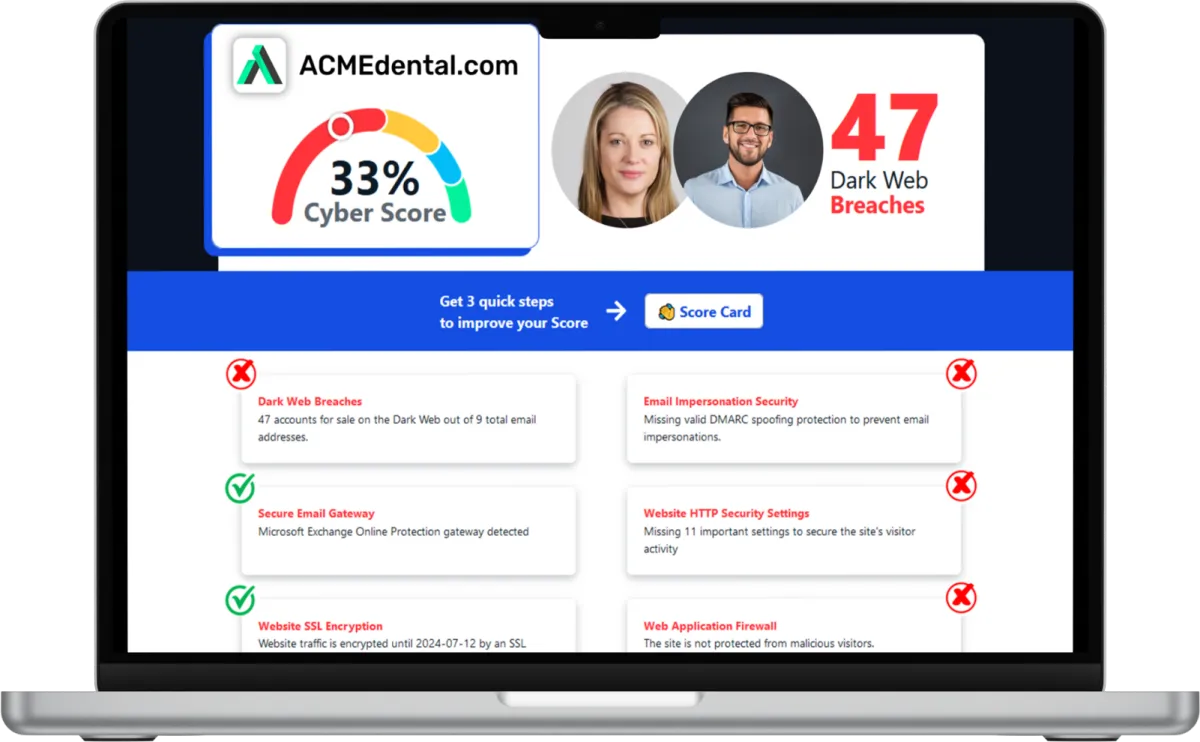
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

Emerging Ransomware Tactics: What You Should Know in 2025
Ransomware is like a burglar who keeps upgrading their tools — picking smarter locks and finding new ways to slip inside unnoticed. In 2025, these digital burglars will be more sophisticated than ever, using tactics like artificial intelligence and double extortion to cause maximum damage.
Staying ahead of these tactics starts with understanding them. This post breaks down the latest ransomware strategies and provides practical tips to help protect your business in this ever-changing landscape.
What Makes Ransomware Different in 2025?
Ransomware in 2025 will be smarter and more targeted than ever before. For instance, Google's research points to the rise of AI. Cybercriminals use AI to craft convincing phishing emails and deploy malware that adapts to evade detection. This makes attacks more challenging to spot and easier to execute.
Double extortion has cemented itself as a leading tactic. Attackers encrypt data and simultaneously exfiltrate it, threatening to leak sensitive information unless their demands are met. This combination significantly raises the stakes for victims, exposing them to financial, reputational, and regulatory risks. By late 2022, 70% of ransomware incidents involved data theft, which continues to rise.
Small to medium-sized businesses (SMBs) are increasingly in the crosshairs. With fewer resources for cybersecurity, SMBs suffer cyber extortion attacks 4.2 times more often than larger enterprises.
Trending Tactics Cybercriminals Use
Cybercriminals constantly refine their methods and utilize new technologies and strategies to maximize their impact. Here are some of the most dangerous ransomware tactics emerging in 2025:
AI-Driven Phishing Emails
Attackers leverage artificial intelligence to craft phishing emails that are virtually indistinguishable from genuine communications. These emails can mimic trusted contacts, including coworkers or service providers, and are personalized to increase their effectiveness.
Exploitation of Remote Work Vulnerabilities
The rise of hybrid and remote work environments has provided cybercriminals with new attack surfaces. Home office setups often lack enterprise-grade security measures, and unsecured personal devices or outdated VPN configurations make them easy entry points. Once inside, attackers can move laterally to access critical business systems.
Ransomware-as-a-Service (RaaS)
RaaS has democratized ransomware operations, enabling even low-skill attackers to launch sophisticated campaigns. Through this model, cybercriminals purchase or lease ready-made ransomware tools from more experienced developers. This increases the frequency of attacks and introduces a wider range of threat actors.
What You Can Do to Stay Secure
Ransomware is evolving, but taking proactive steps can keep businesses ahead of the threats. These include:
Spot Suspicious Emails
Phishing emails are still the most common entry point for ransomware. Verify links and attachments before clicking and watch for red flags like mismatched sender details or unusual requests. If something feels off, reach out to the sender directly using a known contact method.
Use Multi-Factor Authentication (MFA)
MFA adds a critical layer of protection by requiring a second step, like a code sent to your phone, before granting access. Even if passwords are compromised, MFA can block unauthorized logins and secure sensitive systems.
Train Your Team
Employees are your first line of defense. Regular training helps them recognize phishing attempts, avoid clicking on malicious links, and report suspicious activity. Awareness across your team significantly reduces your vulnerability.
Partner with an MSP
Managed IT providers are your cybersecurity allies. They monitor your systems, install updates, and provide tools to detect and block ransomware before it spreads. Regular collaboration with your MSP helps you stay prepared as threats evolve.
Staying Ahead in the Fight Against Ransomware
Ransomware is not going away—it's evolving, growing smarter, and becoming a greater threat to businesses of all sizes. The key to resilience lies in staying informed, proactive, and adaptable. By understanding emerging tactics, you can take the necessary steps to strengthen your defenses.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!





































