Existing Clients: (866) 437-6325
Sales Inquiries: (855) 788-4805
Strategic IT Services
to Secure Your Business
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse.
OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions
Proven Expertise in IT
With deep expertise, we deliver IT solutions prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
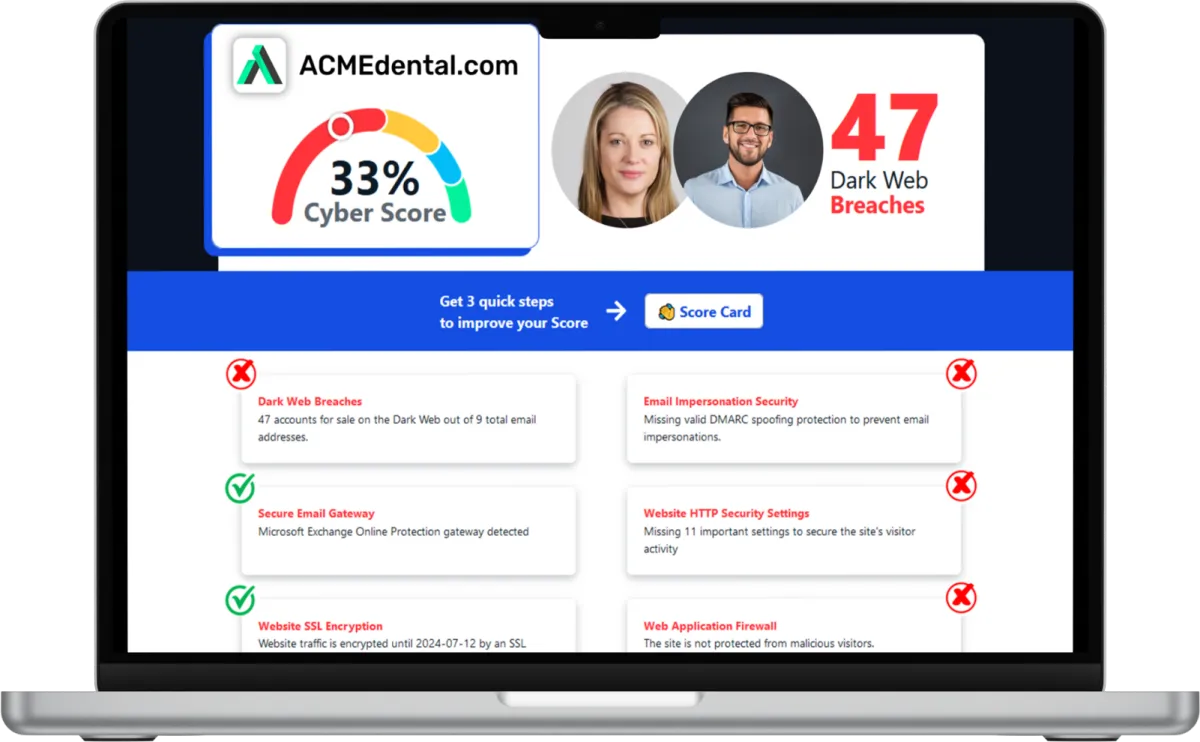
Want to see your Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support solutions.
Are frequent technical problems impacting your business’s success?
With outsourced IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable, proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert support, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business stay resilient, efficient, and secure.

Fraud Prevention in a Digital World: Insights from Joe Ruskey
Fraud is an ever-present threat in today’s digital world. Whether it’s email scams, identity theft, or financial fraud, cybercriminals are always adapting their tactics to exploit individuals and organizations. Joe Ruskey, a cybersecurity expert and Rotarian from La Crosse, Wisconsin, knows this all too well.
While completely stopping fraudsters is impossible, Joe emphasizes that there are effective ways to slow them down and reduce the damage they can cause. His approach? Education, verification, and proactive security measures.
How Can We Minimize Fraud?
According to Joe, the key question we should all ask ourselves is:
“How can we slow fraud down as much as possible or make sure that when it does happen, it’s not as much of a disaster?”
While we may never eliminate fraud completely, being prepared can make all the difference. That means staying vigilant and building layers of protection into our daily digital interactions.
Key Fraud Prevention Strategies
Joe has shared his expertise with Rotary clubs and community organizations, helping them understand how to recognize and prevent scams. His key recommendations include:
1️⃣ Always Verify Contacts
🔹 Double-check emails, phone calls, and messages. Fraudsters often impersonate colleagues, friends, or organizations you trust.
🔹 If a request for money or sensitive information feels unusual, confirm it through a separate communication channel. Call the person directly rather than replying to the email or message.
2️⃣ Vet Requests for Donations
🔹 Scammers often pose as charities, especially during crises or natural disasters.
🔹 Before donating, research the organization and ensure your money is going to a legitimate cause.
3️⃣ Use Multifactor Authentication (MFA)
🔹 A strong password isn’t enough anymore. MFA requires an additional verification step (such as a text message or authentication app) to log in.
🔹 Enable MFA for your financial accounts, business communications, and sensitive platforms to add an extra layer of security.
4️⃣ Be Aware of Social Engineering Tactics
🔹 Cybercriminals don’t just hack computers—they hack people.
🔹 Many fraudsters spend time observing how you communicate, learning names, nicknames, and internal workflows. This makes their scams appear more legitimate.
🔹 Be cautious of urgent or unusual requests—even if they appear to come from someone you trust.
Nobody is Too Small to Be a Target
One of the biggest misconceptions about cyber fraud is that only big corporations or wealthy individuals are targeted. Joe Ruskey warns that scammers go after everyone.
“You have to understand that nobody is too small. They’re coming after everybody. They’re coming after you because you’ve got very valuable data.”
Whether you’re an individual, a small business, or a nonprofit, your data is valuable—and cybercriminals know it. That’s why every person and organization should take fraud prevention seriously.
Final Thoughts: Stay Aware, Stay Secure
Fraud isn’t going away, but we can fight back with awareness, education, and strong security habits. Joe Ruskey’s message is clear: If we take the right precautions, we can significantly reduce the impact of cyber threats.
Take Action Today:
✅ Verify before you trust – Don’t fall for urgent or suspicious requests.
✅ Strengthen your security – Enable MFA and use strong passwords.
✅ Educate yourself and others – Fraud prevention is a shared responsibility.
By taking these steps, we can slow down fraudsters and protect ourselves, our businesses, and our communities. Let’s stay vigilant and keep our networks safe!
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT services that empower your business to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!



































