Client Support: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.

OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
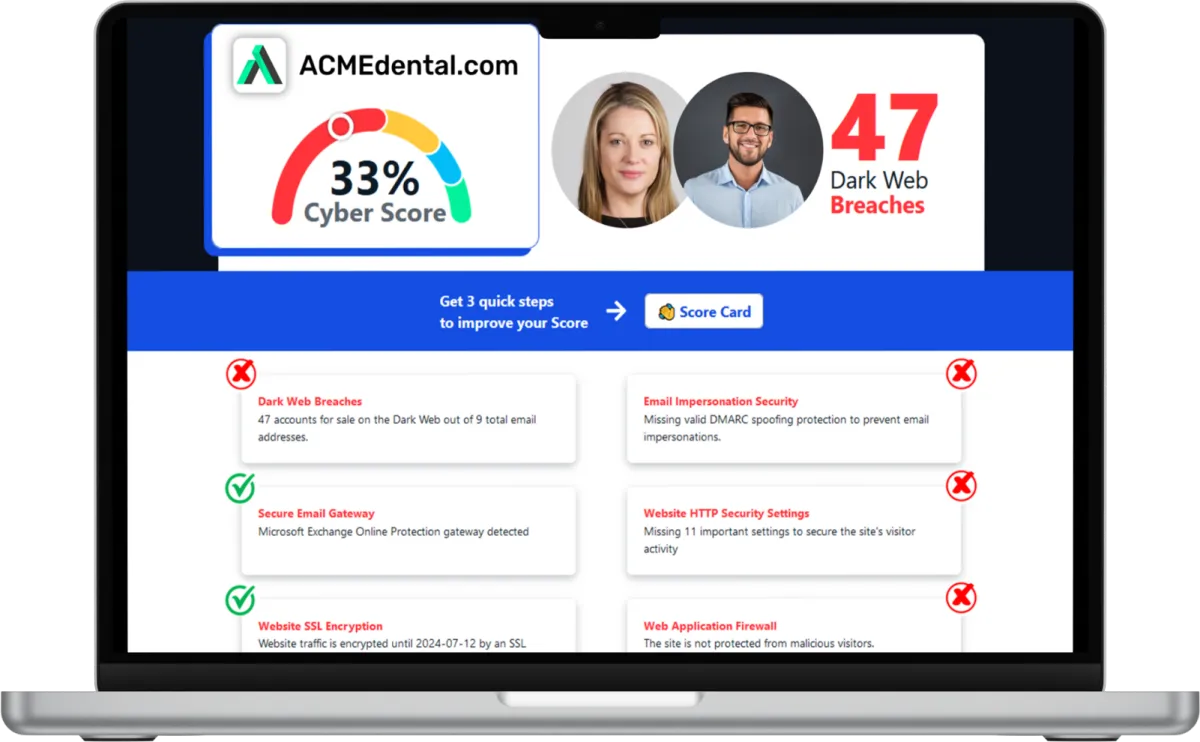
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

How to Protect Your Business from Shadow IT Risk
It's no secret that technology has completely transformed the way we do business. From cloud computing to mobile devices, there are countless tools and resources available to help companies operate more efficiently and effectively.
However, these benefits also come with risks, particularly when it comes to unapproved technology being used at your company. This is known as "shadow IT," and it can pose significant threats to the security and stability of a business.
In this guide, we will discuss what shadow IT is, its potential risks, and, most importantly, how to protect your business. By being proactive and taking the necessary precautions, you can prevent shadow IT from causing harm to your company.
What is Shadow IT?
Shadow IT refers to any technology or software that is used within a company without the approval or knowledge of the IT department. This can include everything from personal smartphones and laptops to cloud services and productivity apps.
Essentially, anything that is not officially sanctioned or supported by the company's IT team falls under the umbrella of shadow IT. And, with the rise of remote work and the increasing accessibility of technology, it's only becoming more prevalent in the workplace. In fact, a study by Gartner found that 41% of employees reported using unauthorized tech for work purposes.
Why Does Shadow IT Happen?
So why do employees turn to shadow IT in the first place? It's not usually out of malicious intent; instead, it's often due to:
Convenience: Employees may find unapproved tools easier or faster to use than official ones, especially if they feel the approved solutions are outdated or cumbersome.
Productivity: Some employees believe that using their preferred apps or devices will help them work more efficiently or collaborate more effectively.
Lack of Awareness: In some cases, employees don't realize the risks associated with using unauthorized technology or may not even be aware of company policies regarding approved tools.
Gaps in IT Support: When employees feel their needs aren't being met by the IT department, they may take matters into their own hands to find solutions.
The Risks of Shadow IT
While it may seem harmless on the surface, shadow IT can bring many risks and challenges to a business. These include:
Security Vulnerabilities
Using unapproved tools can expose a company's sensitive data to security breaches and cyberattacks. Shadow IT often lacks the necessary security protocols and updates, leaving systems vulnerable to hackers.
Reduced Visibility and Control
With people using different tools and devices, it becomes challenging for the IT team to track and manage all technology in use. This lack of control can make enforcing compliance with regulations or company policies difficult.
Data Silos and Loss
When employees use their own tools and devices, relevant data may not be shared with the rest of the team or backed up on company servers. This can lead to data silos, making it difficult for teams to collaborate and causing loss of important information.
Increased IT Costs
Tracking and addressing unauthorized technology retroactively can strain IT resources and increase costs. Fixing issues caused by shadow IT often takes time and effort that could have been avoided with proper oversight.
How to Protect Your Business from Shadow IT
Addressing shadow IT requires a proactive approach. Here's how you can safeguard your business while empowering employees with the tools they need:
Foster Open Communication
Create a culture where employees feel comfortable discussing their technology needs. By understanding their challenges, companies can recommend suitable tools and eliminate the need for shadow IT.
Develop Clear Policies
Establish and communicate clear guidelines on what technology and tools are approved for use. Include explanations of why these policies are essential to the company's security and compliance.
Provide User-Friendly Tools
Ensure that approved tools and systems are intuitive, efficient, and capable of meeting employee needs. Conduct regular surveys or feedback sessions to assess satisfaction with the current tech stack.
Educate Your Team
Train employees on the risks of shadow IT and the importance of using approved tools. Provide practical examples of how shadow IT can lead to security breaches or compliance issues.
Use Monitoring Software
Deploy monitoring tools to track the use of unapproved apps and devices. While this shouldn't replace trust, it can provide insights into potential risks and help you address them quickly.
Take Control of Shadow IT
Shadow IT doesn't have to be a looming threat to your business. By understanding why it happens and taking proactive measures to address it, you can mitigate risks while fostering a secure, productive work environment.
Remember, the goal isn't to stifle innovation but to strike a balance between empowering employees and maintaining control over your company's technology landscape. So, take steps today to protect your business from the hidden risks of shadow IT.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!





































