Existing Clients: (866) 437-6325
Sales Inquiries: (855) 788-4805
Strategic IT Services
to Secure Your Business
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse.
OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions
Proven Expertise in IT
With deep expertise, we deliver IT solutions prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
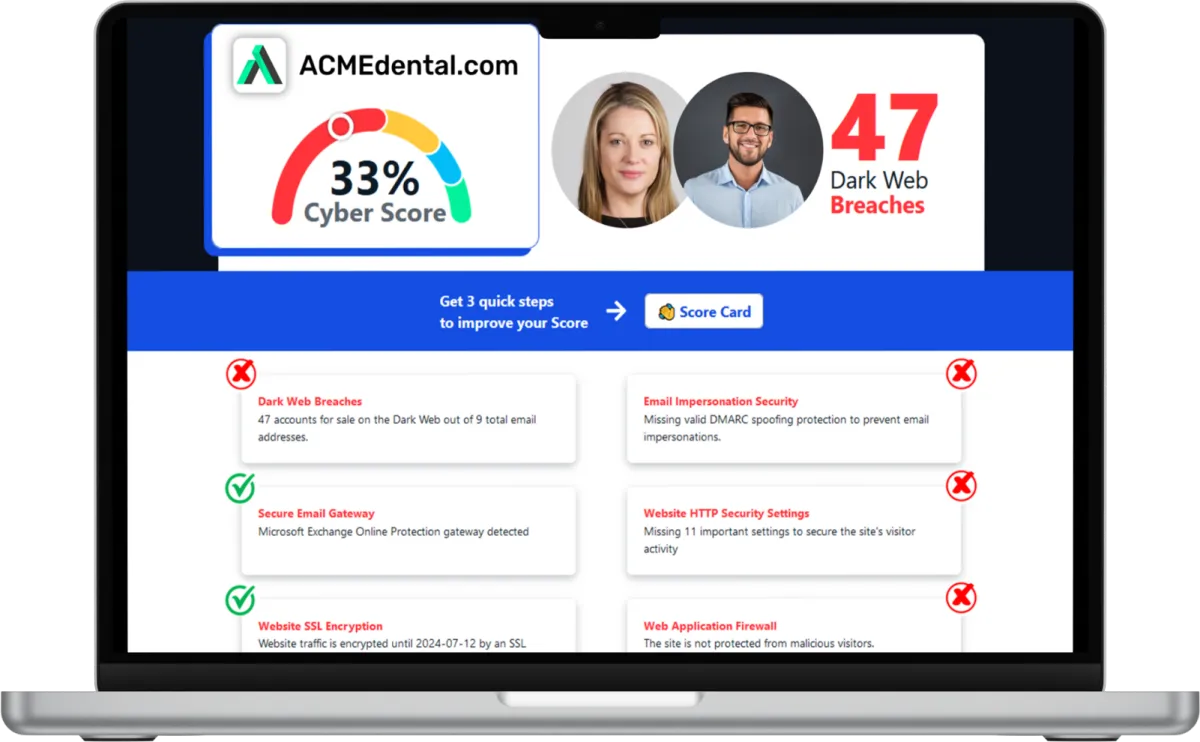
Want to see your Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support solutions.
Are frequent technical problems impacting your business’s success?
With outsourced IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable, proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert support, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business stay resilient, efficient, and secure.

Spring Cleaning for Your Digital Workspace: Organizing Files and Streamlining Tools
When you think of spring cleaning, your mind probably jumps to decluttering your closet or cleaning out the garage. But what about your digital workspace? Just like your physical surroundings, your digital spaces also need regular attention to keep them functioning at their best.
Over time, your tech systems can become cluttered with outdated software, unused accounts, and unnecessary files. This not only hinders productivity but also poses a security risk. The start of spring is the perfect time to tackle these issues and refresh your digital workspace.
Ready to get started? Let's dive into how you can clean up your digital space and set your business up for success.
1) Audit Your Software and Applications
According to a 2024 Zylo Report, around 51% of software licenses go unused by businesses. This isn't just a waste of money—it's also a potential security risk.
Start by creating an inventory of all the software and applications your business uses. Ask yourself:
Do we still need this?
Is there a newer version available?
Are there any duplicate programs that can be consolidated?
Uninstall any outdated or unnecessary software to free up space and reduce vulnerabilities. For the tools you consistently utilize, keep them updated to the latest versions to ensure optimal performance and security.
2) Organize Your Digital Files
Just like physical clutter can hinder productivity, so can digital clutter. Take some time to go through your files and folders, deleting any outdated or unnecessary documents. Create a clear and organized filing system to help you quickly locate important files when needed.
You can also automate this process by using tools like file management software or cloud storage solutions. These tools allow you to easily organize your files, access them from anywhere, and back them up in case of any unexpected data loss.
3) Review User Accounts and Permissions
Do you have any "zombie accounts" lurking in your system? These are inactive user accounts that still have access to your network or software, making them prime targets for malicious activity. To minimize risk, regularly review and revoke access for former employees or contractors.
Also, take a close look at the permissions for current users. Does everyone really need access to every file and folder? Probably not. Restricting access based on roles reduces the risk of unauthorized access and keeps your sensitive information secure.
4) Evaluate Your Hardware
Just as software can become outdated, so can hardware. Assess the condition and performance of your equipment, including servers, computers, and networking devices. If any hardware is nearing the end of its lifecycle, start planning for replacements to avoid unexpected downtime.
An MSP can help you determine if it's time to upgrade your hardware and can also assist with the implementation process. They can also provide recommendations for cost-effective solutions, such as transitioning to cloud-based services.
5) Streamline Your Communication Channels
Having too many communication channels can lead to confusion and inefficiency. Take stock of the different platforms your team uses for communication, such as email, messaging apps, and project management tools. Consider consolidating them into one or two main channels to streamline communication and ensure important messages don't get lost in the noise.
You can also set guidelines for when each channel should be used—for example, using email for formal communications and a messaging app for quick questions or updates. This will help reduce distractions and keep everyone on the same page.
6) Plan for Future Growth
Finally, take this time to plan for the future. Consider your long-term goals and identify any potential roadblocks or areas for improvement.
Perhaps it's time to upgrade your hardware or invest in new software. Maybe you need to expand your team or outsource additional tasks. Use this opportunity to strategize and set a clear direction for your tech infrastructure.
Keep the Momentum Going
Once your digital systems are clean and organized, commit to maintaining them. By making IT maintenance a habit, you'll keep your business running smoothly year-round. So don't wait any longer—start decluttering and optimizing your tech today!
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT services that empower your business to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!



































