Client Support: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.

OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
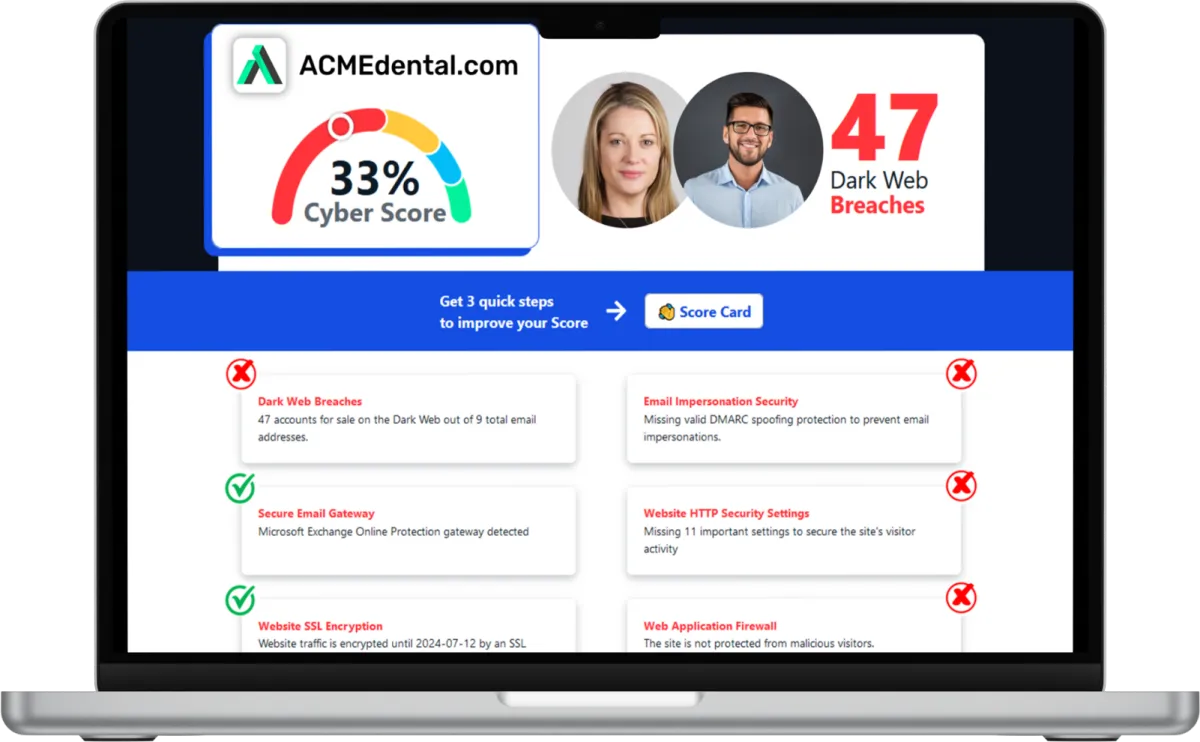
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

The Truth About Shadow IT
Not every cyber risk comes from the outside. Some walk right in the front door ... in the form of tools, apps, and devices your own employees are using without asking.
It’s called shadow IT. And it’s probably already happening in your business.
What Is Shadow IT?
Shadow IT is any tech your employees use for work that your IT team didn’t approve or doesn’t know about.
It could be:
A personal Gmail account for work emails.
A free file-sharing app instead of the company-approved one.
A laptop they bought themselves and set up their way.
An unapproved project management tool “just for this one team.”
None of it goes through your IT department. None of it is monitored, patched, or secured the way your approved systems are.
Why It Happens
Most employees don’t do this to cause trouble. In fact, their reasons usually make sense:
Convenience — The approved tool feels slow, clunky, or outdated.
Productivity — The new app they found “just works better” for them.
Lack of Awareness — They don’t see the harm in using a personal account or tool.
IT Gaps — They need a solution now and don’t think IT will move fast enough.
The problem is… even the best intentions can open the door to a mess.
The Risks You Can’t See
Shadow IT is dangerous because it’s invisible until something goes wrong.
Security Holes — Unapproved tools rarely meet your security standards. They may be missing critical updates or store data in unsafe ways.
No Oversight — If IT doesn’t know a tool exists, they can’t monitor it, patch it, or protect it.
Data Loss & Silos — Information gets trapped in personal accounts or tools that aren’t backed up, making collaboration harder and risking permanent loss.
Regulatory Trouble — Sensitive data stored in unauthorized apps can violate compliance rules — without you even realizing it.
Wasted IT Costs — Fixing a shadow IT– caused by a security incident takes far more time and money than preventing it in the first place.
How to Keep It From Becoming a Disaster
You can’t stop what you can’t see ... so start by making shadow IT a conversation, not a witch hunt.
Foster Open Communication
If employees feel like IT will say “no” to everything, they’ll stop asking. Make it safe to bring up new tech needs. The earlier you know, the faster you can approve or suggest safer alternatives.Set Clear Policies
List which tools are approved ... and why. When employees understand the security and compliance stakes, they’re less likely to go rogue.Make Approved Tools Worth Using
If your official tools are slow, outdated, or frustrating, shadow IT will fill the gap. Invest in solutions that are intuitive, reliable, and actually make people’s jobs easier.Train Your Team
Most people don’t realize that using an unapproved app can lead to a breach. Show real-world examples of how it happens and the damage it can cause.Monitor Without Micromanaging
Use monitoring tools to spot unauthorized apps and devices. The goal isn’t to spy ... it’s to flag risks before they turn into incidents.
The Bottom Line
Shadow IT isn’t just a tech problem ... it’s a business risk that grows quietly until something breaks. The solution isn’t banning everything employees want to use ... it’s balancing innovation with control.
When you give people the tools they need, communicate the risks clearly, and keep visibility over your tech environment, shadow IT goes from a hidden threat to a manageable challenge.
If you’re already a client, we’re monitoring and securing against this risk every day. If you’re not, shadow IT could be costing you in ways you can’t yet see ... until it’s too late.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!




































