Client Support: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.

OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
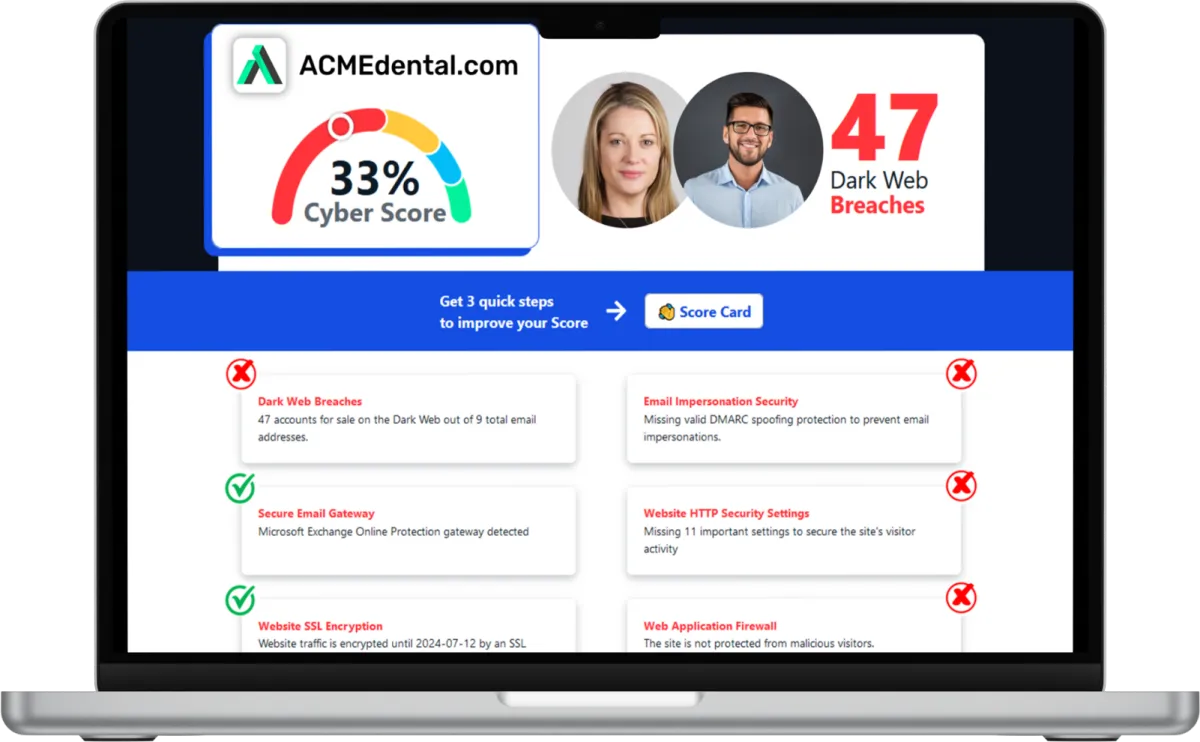
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

The Significance of Endpoint Security
With the increasing number of cyber threats targeting endpoints, businesses must prioritize endpoint protection to safeguard their clients' sensitive data and ensure uninterrupted business operations.
In this blog, we will delve into the growing significance of endpoint security and explore why you need to make it a top priority.
5 Reasons You Can’t Overlook Endpoint Security
Protection Against Malware
Endpoint security is crucial for businesses as it provides a robust defense against malware threats. With advanced detection and prevention mechanisms, it safeguards endpoints from malicious software that can compromise sensitive data and disrupt operations.
Data Loss Prevention
Endpoint security helps prevent data breaches and loss by implementing encryption, access controls, and data backup solutions. By securing endpoints, businesses can ensure the confidentiality, integrity, and availability of their critical information assets.
Mitigating Insider Threats
Endpoint security plays a vital role in mitigating insider threats by monitoring and controlling user activities. It helps detect and prevent unauthorized access, data exfiltration, and malicious insider actions, reducing the risk of internal breaches.
Safeguarding Remote Workforce
With the rise of remote work, endpoint security becomes even more critical. It protects endpoints outside the traditional network perimeter, securing devices, and data regardless of their location, ensuring a secure remote work environment.
Compliance and Regulatory Requirements
Endpoint security is essential for businesses to meet compliance and regulatory requirements. It helps enforce security policies, track and report security incidents, and demonstrate adherence to industry-specific regulations, avoiding penalties and reputational damage.
How To Select Your Endpoint Security
Evaluate Comprehensive Protection
Look for an endpoint security solution that offers a wide range of features, including:
Real-time threat detection
Advanced malware protection
Firewall capabilities
Data encryption
A comprehensive solution ensures holistic protection for your business.
Consider Scalability and Compatibility
Ensure that the endpoint security solution can scale with your business growth and is compatible with your existing IT infrastructure. It should seamlessly integrate with your network and support various operating systems and devices to provide consistent protection across all endpoints.
Prioritize User-Friendliness
Opt for an endpoint security solution that is easy to deploy, manage, and use. A user-friendly interface and intuitive controls will save time and effort for your IT team, allowing them to focus on other critical tasks.
Assess Performance and Resource Impact
Test the solution's performance impact on endpoints and system resources. It should provide robust security without significantly slowing down devices or causing disruptions. Look for solutions that offer efficient resource utilization and minimal impact on user productivity.
Don’t Let Your Unsecured Endpoints Put You At Risk
As the threat landscape continues to evolve, businesses must adapt and prioritize endpoint security to stay one step ahead of cybercriminals. By implementing robust endpoint protection measures, businesses can mitigate risks, protect sensitive data, and maintain a secure computing environment.
Remember, endpoint security is not just an option; it is a necessity in today's digital age. So, let's embrace the growing significance of endpoint security and work together to build a resilient and secure IT infrastructure for businesses of all sizes.
If you need expert assistance deploying or managing your endpoint security measures, reach out to our team.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!





































