Client Support: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.

OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
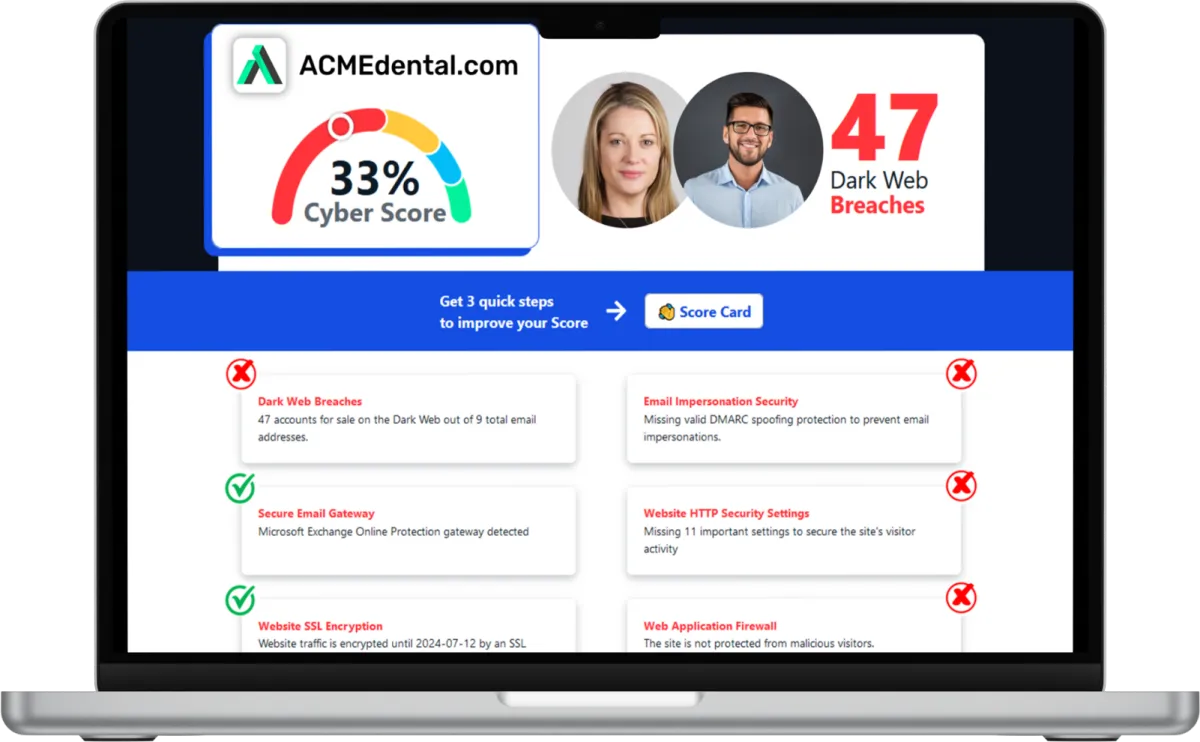
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

6 Habits That Quietly Decide If Hackers Win or Lose
Most cyberattacks don’t start with a mastermind hacker running lines of code in some movie-style lair. They start with something small.
A sticky note with a password written on it.
A rushed click on a link that “looked fine.”
A laptop left unlocked while its owner grabs a coffee.
One moment like that can undo every dollar your business has invested in security. And the scary part? Hackers count on these moments. They know technology is only half the battle the other half is human behavior.
The good news? The same way one bad habit can open the door, one good habit can keep it shut. And if your whole team follows these six, you’ll be miles ahead of the companies that don’t.
1. Stop Writing Down Passwords
Passwords are like house keys they only work if you keep them safe. The moment yours ends up on a Post-it or in an unprotected file, it’s like leaving a copy of your front door key under the welcome mat.
Hackers know this. Anyone who sees that note, even for a second, can access your accounts.
Instead:
Memorize your passwords or use a reputable password manager.
Don’t reuse passwords between accounts.
Keep them out of email, chat, and shared documents.
2. Think Before You Click
Most phishing attacks don’t look like scams at first glance. They’re designed to look familiar, urgent, and legitimate; a shipping notice, a client request, a security alert.
That’s why hackers love busy people. The more distracted you are, the more likely you’ll click without checking.
Before you click:
Hover over the link to see the real destination.
Check the sender’s email address for typos or weird domains.
If it feels off, confirm through a separate channel before acting.
3. Report Weird Stuff Right Away
This is one of the simplest, most effective defenses… and one of the most ignored.
If something looks suspicious; an odd email, a strange pop-up, your computer suddenly slowing down tell your IT team now. Don’t wait until after lunch. Don’t assume “it’s probably nothing.”
Early reports can turn a potential breach into a quick fix. Delays give threats time to spread.
4. Don’t Plug in Random USB Drives
That free flash drive from a trade show? It might come with malware as a bonus. Dropped-in-the-parking-lot USB drives are a known hacker tactic.. they rely on curiosity or convenience to get you to plug them in.
The second you do, you’ve bypassed most of your company’s digital defenses.
Safer approach: Only use devices issued or approved by your company. If you don’t know where it came from, don’t connect it.
5. Keep Work Devices for Work Only
It’s tempting to stream a movie, shop online, or install a personal app on your work laptop. But every non-work activity increases your exposure to malicious websites, shady downloads, and compromised accounts.
When you use work tech for personal use, you’re mixing trusted business systems with unverified sources.. and hackers love that.
Draw a hard line: work devices are for work tasks, personal devices are for personal use.
6. Lock Your Screen Every Time You Walk Away
Even a quick trip to the break room is enough time for someone to access your computer. It doesn’t have to be malicious.. even a curious glance at the wrong file can cause problems.
Make it second nature to lock your screen whenever you step away. Learn the keyboard shortcut for your system and use it without thinking.
The Bottom Line
Technology can stop a lot of threats, but it can’t fix bad habits. Every employee is part of the security team whether it’s in their job description or not.
The companies that avoid costly breaches aren’t just the ones with the best firewalls; they’re the ones whose people build good security habits into their daily routine.
If you’re a client, these habits are reinforced in our training and systems. If you’re not, this list is your starting point. Because in the end, the difference between stopping an attack and suffering through one often comes down to small choices made in seconds.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!





































