Existing Clients: (866) 437-6325
Sales Inquiries: (855) 788-4805
Secure IT Support
Strategic IT Support
in La Crosse and Throughout the Midwest
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse and throughout the Midwest.
OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions for IT Support in La Crosse
Proven Expertise in IT
With deep expertise, we deliver IT Support in La Crosse, prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent IT support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
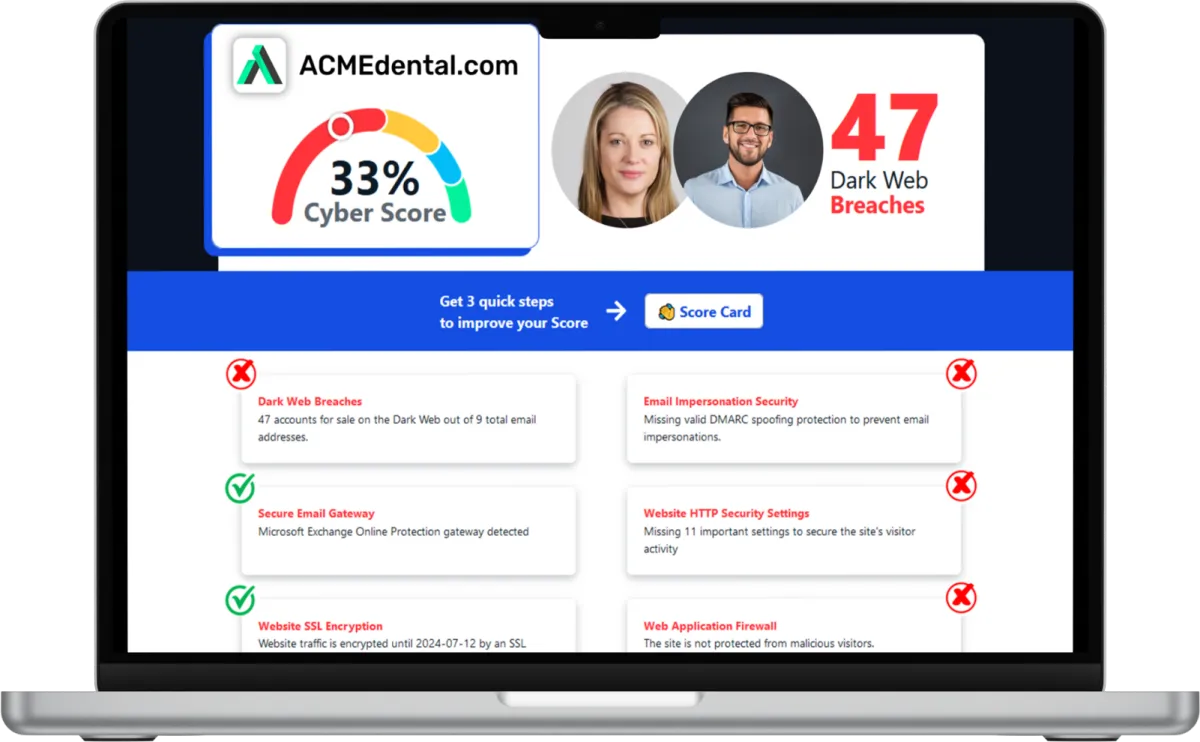
Want to see your Cyber Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your La Crosse Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support in La Crosse.
Are frequent technical problems impacting your business’s success?
With IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable's IT Support in La Crosse offers proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert IT support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert IT support in La Crosse, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated IT support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business in La Crosse stay resilient, efficient, and secure.

Protecting Your Personal Devices: Cybersecurity Tips for Home and Beyond
Your phone is more than a phone. It is a wallet, a filing cabinet, a work desk, and a personal vault—and hackers know it. The same goes for laptops and tablets, which store everything from financial records to business emails.
Cyber threats are no longer confined to corporate networks. Personal devices are prime targets, and one weak link can put both personal and professional data at risk. Ransomware and extortion incidents surged by 67% in 2023, showing just how aggressively cybercriminals are targeting individuals and businesses alike.
With remote work, cloud access, and bring-your-own-device policies, the line between personal and business security has blurred. A single compromised device can expose sensitive company data, making cybersecurity a shared responsibility, not just an IT department problem.
The good news is that protecting personal devices does not have to be complicated. This guide will show you how to stay safe, whether at home, on public networks, or anywhere in between.
Keep Devices Updated
Hackers love outdated software. When a device runs on an old operating system, or an app has not been updated in months, it becomes an easy target for cybercriminals looking to exploit security gaps.
Many cyberattacks take advantage of known vulnerabilities—issues that have already been patched in newer updates. If a device is behind on updates, it essentially leaves the front door wide open.
To prevent any issues, turn on automatic updates for your operating system, apps, and security software so you never miss a fix. Beyond that, regularly update browsers, firmware, and plugins, especially for tools that handle sensitive data. Even a small delay in patching can leave a system exposed.
Use Strong Authentication
A weak password is like a flimsy lock on your front door. It might keep out casual intruders, but a determined hacker can break in with minimal effort.
Password breaches are one of the most common ways cybercriminals gain access to personal and business data. Once they crack one account, they often try the same password on other platforms, making reused passwords a huge security risk.
One of the best ways to prevent unauthorized access is by enabling multi-factor authentication (MFA) on important accounts, such as banking, email, and cloud storage. MFA requires a second form of verification, like a fingerprint or a one-time code, making it significantly harder for hackers to break in, even if they steal a password.
You also need strong, unique passwords for every account. Avoid simple, predictable choices like "password123" or birthdays. Consider using a password manager to generate and store complex credentials securely.
Secure Your Internet Connection
An internet connection is only as secure as the network it runs on. Unsecured Wi-Fi makes it easy for hackers to intercept sensitive information, steal credentials, and even take control of connected devices. Without proper security, cybercriminals can exploit weak routers, spy on internet traffic, or plant malware on a device before a user even realizes what happened.
To protect your network, start by using strong encryption on your home Wi-Fi. Modern routers support WPA3 encryption, which provides better protection against cyber threats than older WPA2 or WEP standards. Changing the default router password is also essential since many factory-set credentials are easy for attackers to guess.
Public Wi-Fi poses another major risk. If you must access sensitive accounts while on an unsecured network, use a VPN to encrypt your data and prevent unauthorized snooping.
Watch Out for Phishing and Scams
Hackers do not need sophisticated tools to steal data when they can simply trick people into handing it over. Phishing scams remain one of the most effective cyberattacks because they rely on deception rather than technical exploits.
Cybercriminals send fake emails, text messages, or create bogus websites designed to steal passwords, financial details, or other sensitive information. Clicking the wrong link or entering credentials on a fraudulent site can give hackers full access to personal and business accounts.
The best defense against phishing is caution. Research conducted in 2023 found that 10.4 percent of employees worldwide clicked on malicious links, and over 60 percent of those who clicked went on to submit a password on fake websites. This highlights just how easy it is for phishing scams to succeed.
Always think before you click on email links, especially those claiming to be from banks, subscription services, or government agencies. If an email asks for personal details or urges immediate action, it is a red flag. Before entering any information, check for HTTPS in the URL to confirm the site is secure.
Digital Security Is a Habit, Not a Task
Cybersecurity is not a one-time fix. It is a mindset, a habit, a way of engaging with technology that prioritizes caution over convenience. The devices we carry are vaults of personal and professional data, gateways to financial accounts, and, if left unprotected, invitations to cybercriminals.
Security does not have to be complicated, but it does have to be intentional. Updating software, enabling MFA, securing networks, and thinking twice before clicking are not just best practices—they are digital self-defense. Just as we lock our doors at night without a second thought, protecting our personal devices should be second nature.
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support in La Crosse with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT Support that empower your business in La Crosse to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!



































