Existing Clients: (866) 437-6325
Sales Inquiries: (855) 788-4805
Strategic IT Services
to Secure Your Business
Dependable Solutions strengthens client operations with reliable, comprehensive outsourced IT support in La Crosse.
OUR EXPERT TEAM KEEPS YOU SECURE AND COMPLIANT
Why Businesses Choose Dependable Solutions
Proven Expertise in IT
With deep expertise, we deliver IT solutions prioritizing proactive management and performance optimization.
Dedicated Customer Service
We value our clients above all, providing consistent support that addresses unique challenges and aligns with your goals.
Swift Issue Resolution
Our responsive team minimizes disruptions, addressing problems at the source to ensure smooth, efficient operations.
Comprehensive Cybersecurity Protection
We defend your business with advanced cybersecurity, proactive monitoring, and regular assessments that safeguard your network, helping you focus on what matters most.
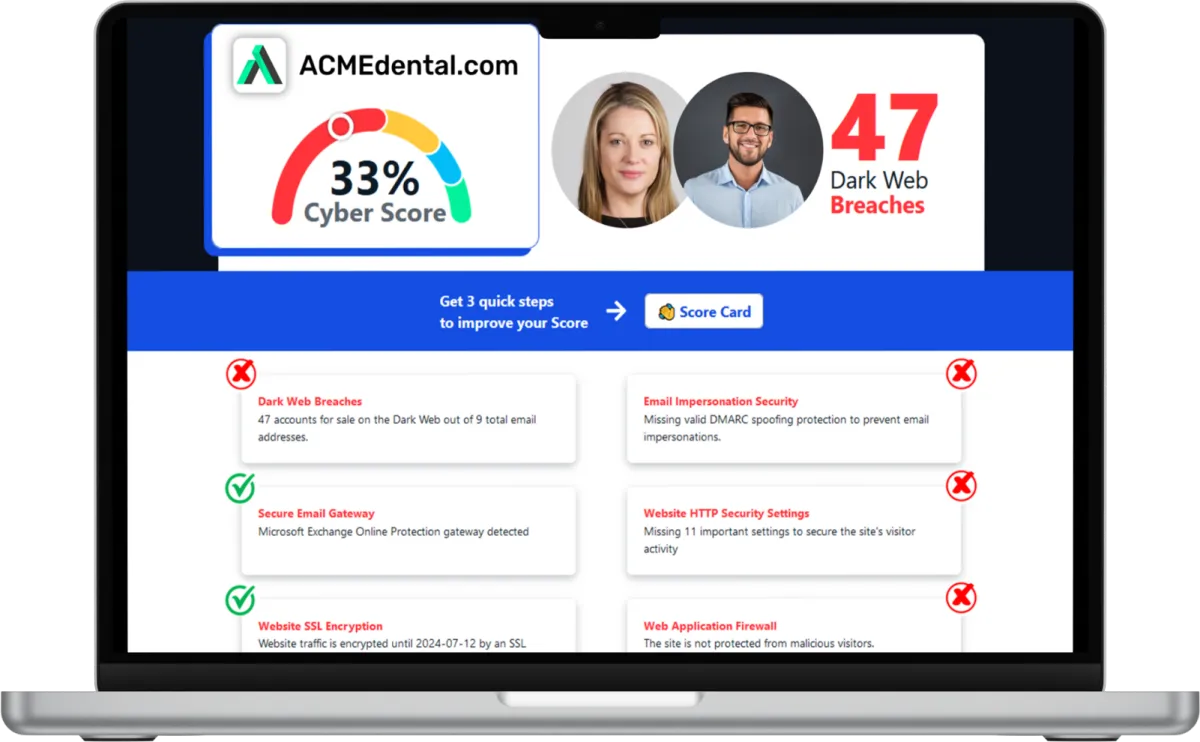
Want to see your Score?
Get it in 30 seconds!
Struggling with IT Roadblocks that Slow Your Business Down?

Joe Ruskey
CEO, Dependable Solutions
Dependable Solutions is Here to Help.
When technology issues repeatedly disrupt your workflow, productivity suffers, and resources are drained. Dependable Solutions can help you overcome these challenges with proactive, customized IT support solutions.
Are frequent technical problems impacting your business’s success?
With outsourced IT support in La Crosse, Dependable Solutions tackles your technology needs, addressing critical pain points and improving your daily operations. Our team provides efficient, security-focused support, so you can concentrate on driving your business forward without IT setbacks. Reach out today for reliable, comprehensive IT solutions to protect and streamline your business.
Call (855) 788-4805 today to schedule your appointment. We’re ready to start important IT conversations with businesses just like yours.
How Can We Help?
Our Services
Dependable, proactive IT management that optimizes uptime and supports consistent, efficient operations tailored to your business’s performance needs.
Strengthen your in-house IT with expert support and resources, ensuring flexibility, scalability, and resilience across your operations.
Layered cybersecurity measures that minimize risk, protect your data, and fortify your network against evolving cyber threats.
Detailed continuity planning that protects operations, reduces downtime, and ensures seamless performance, even during critical events.
Seamlessly migrate to Azure with expert support, optimizing your cloud infrastructure for enhanced performance, security, and scalability.
Dedicated support for troubleshooting, guidance, and quick resolutions that keep your daily operations running smoothly.
What Clients Say About Us
Industry Insights and IT Best Practices
Stay informed on IT strategies, security tips, and industry insights to help your business stay resilient, efficient, and secure.

Emerging Ransomware Tactics: What You Should Know in 2025
Ransomware is like a burglar who keeps upgrading their tools — picking smarter locks and finding new ways to slip inside unnoticed. In 2025, these digital burglars will be more sophisticated than ever... ...more
Cybersecurity
February 13, 2025•3 min read

Romance Scams in the Digital Age: How Cybercriminals Exploit Valentine's Day
Valentine's Day is obviously a prime season for these schemes. Scammers prey on heightened emotions and the desire for connection, crafting fake personas and fabricating stories to deceive unsuspectin... ...more
Cybersecurity
February 07, 2025•5 min read

Cybersecurity for Remote Teams: Tips to Keep Your Business Safe
The rise of remote and hybrid work arrangements has been a game-changer for businesses of all sizes. From increased productivity and flexibility to cost savings, the benefits of remote work are undeni... ...more
Cybersecurity
January 09, 2025•4 min read
Frequently Asked Questions
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include, but are not limited to, network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What are managed IT service providers?
Managed IT service providers offer outsourced IT management and support, handling a company's technology needs so the business can focus on core operations.
What are the benefits of cybersecurity services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
Experience Reliable IT Support with Dependable Solutions
Dependable Solutions is dedicated to providing trustworthy, secure IT services that empower your business to operate smoothly and grow confidently. Partner with us for dependable, proactive support that aligns with your unique goals and challenges.
Call (855) 788-4805 today or click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
Subscribe to our newsletter
Subscribe to our newsletter for exclusive updates and insights delivered straight to your inbox!


































